Application vulnerability scan is the superhero of cybersecurity, swooping in to identify weaknesses in your software before the bad guys do. With the digital landscape constantly evolving, ensuring your applications are secure is more critical than ever, and these scans play a key role in keeping you one step ahead.
This process involves a thorough examination of your applications, looking for known vulnerabilities, misconfigurations, and potential exploits. By conducting regular scans, organizations not only protect sensitive data but also maintain trust with their users and clients. It’s a proactive approach that should be on everyone’s radar.
Hey there! Let’s dive into the fascinating world of technology and how it has evolved over the years. Buckle up, because this is going to be a wild ride through time!
Ancient Innovations
Believe it or not, technology isn’t just a modern phenomenon. It all started way back in ancient times when humans first discovered the power of tools. Think about it: the wheel, the lever, and early farming tools were all groundbreaking innovations that shaped the way societies developed. These inventions laid the groundwork for the future, enabling humans to manipulate their environment in ways they never thought possible.
Imagine the excitement of someone seeing a wheel for the first time! Talk about a game changer!
The Industrial Revolution: A Turning Point
Fast forward to the 18th and 19th centuries, and we hit the Industrial Revolution, a period that brought about massive changes in manufacturing processes. The invention of steam power led to the rise of factories, changing the landscape of work forever. People moved from rural areas to cities, and life as they knew it transformed dramatically. The introduction of machines not only increased production rates but also improved efficiency.
It was like hitting the fast-forward button on progress! But let’s not forget, this came with challenges like labor exploitation and environmental concerns, sparking debates that continue today.
The Age of Electricity
With the dawn of the 20th century, electricity began to weave its magic into everyday life. Remember those black-and-white movies? Well, they wouldn’t exist without the invention of the electric light bulb! Thanks to pioneers like Thomas Edison, homes were illuminated, and life got a serious upgrade. This era also saw the rise of telecommunication, with the telephone revolutionizing how people connected.
The world was getting smaller, and the pace of life was picking up like never before!
Computers: The Digital Revolution
Now let’s talk about computers. The 1940s and 50s marked the beginning of the digital age. From massive room-sized machines that filled entire buildings to the sleek laptops we carry today, computers have come a long way. The invention of the microprocessor in the 1970s was a major milestone, enabling the development of personal computers. With this innovation, technology became accessible to the average person, paving the way for the tech-savvy world we live in today.
The Internet: Connecting the World
And then, BOOM, enter the internet in the 1990s. This was the ultimate game changer! Suddenly, information was at our fingertips, and we could connect with people across the globe in an instant. Social media, online shopping, streaming services… you name it! The internet has transformed how we communicate, work, and entertain ourselves. But let’s be real, it’s not all rainbows and butterflies.
Cybersecurity issues and misinformation have become significant challenges that we need to navigate.
The Rise of Smartphones
As we rolled into the 2000s, smartphones emerged and took the world by storm. Remember when flip phones were all the rage? Yeah, those days are long gone. Today, we have powerful mini-computers in our pockets that do everything from taking stunning photos to managing our schedules. The smartphone revolution changed the way we live our lives, blending the digital and physical worlds seamlessly.
Honestly, it’s hard to imagine a day without checking our phones!
Artificial Intelligence: The Future is Here
Now, let’s talk about one of the most exciting developments happening right now: artificial intelligence (AI). From personal assistants like Siri and Alexa to advanced machine learning algorithms that can analyze data faster than we can blink, AI is reshaping industries and our daily lives. It’s like having a super-smart buddy who can help us make decisions or automate tedious tasks.
However, it’s crucial to remember the ethical implications that come with such powerful technology. As AI continues to evolve, we need to think about how it affects jobs, privacy, and society as a whole.
Sustainability and Technology
As we look towards the future, one of the biggest challenges we face is sustainability. With technology advancing at breakneck speed, it’s essential to ensure that we’re not harming the planet in the process. Innovations in renewable energy, electric vehicles, and sustainable materials are becoming increasingly important. It’s all about finding that balance between progress and preservation. We have the tools to create a better future; we just need to use them wisely!
Conclusion: The Journey Continues
So, there you have it! A whirlwind tour through the evolution of technology. From ancient tools to AI and beyond, each era has brought new challenges and opportunities, shaping the world we live in today. As we continue this journey, let’s stay curious, embrace change, and work towards a future where technology enhances our lives without compromising our values or the health of our planet.
Here’s to the next chapter in the story of technology!

User Queries
What is an application vulnerability scan?
It’s a process that identifies weaknesses in applications to prevent security breaches.
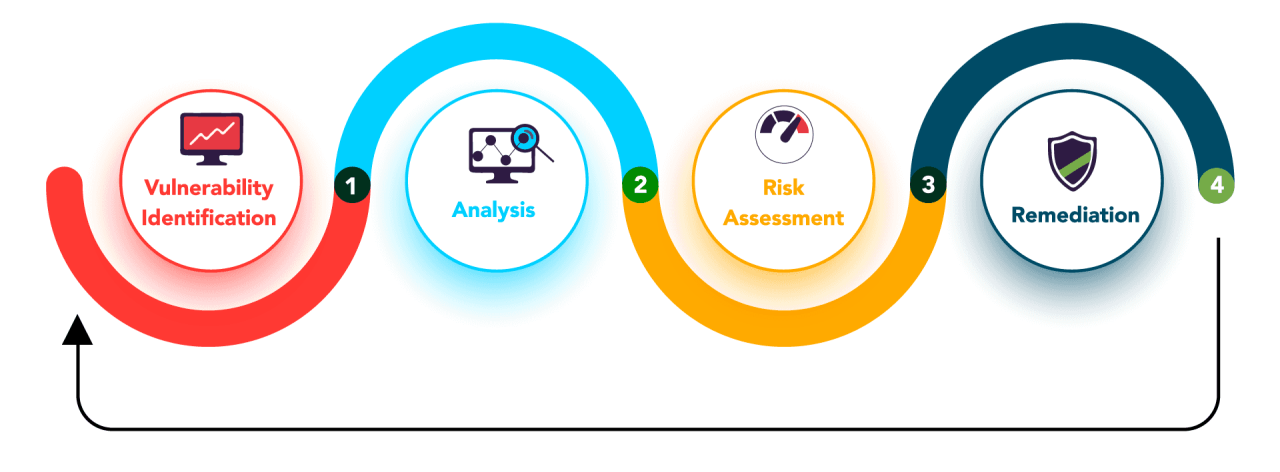
How often should I perform a vulnerability scan?
Regular scans are recommended, ideally quarterly or after significant changes to your applications.
What tools can I use for an application vulnerability scan?
Popular tools include OWASP ZAP, Nessus, and Burp Suite, among others.
Are vulnerability scans enough for security?
No, they should be part of a comprehensive security strategy that includes monitoring and patch management.
Can I perform these scans myself?
Yes, but it’s often advisable to involve professionals for thorough analysis and remediation.